EMPOWER YOUR PEOPLE
95% of data breaches involve human error*
It’s time to empower and secure your workforce by making your staff more resilient to cyber threats, and helping to protect your customers by making your business less susceptible to brand impersonation.
*IBM Cyber Security Intelligence Index Report
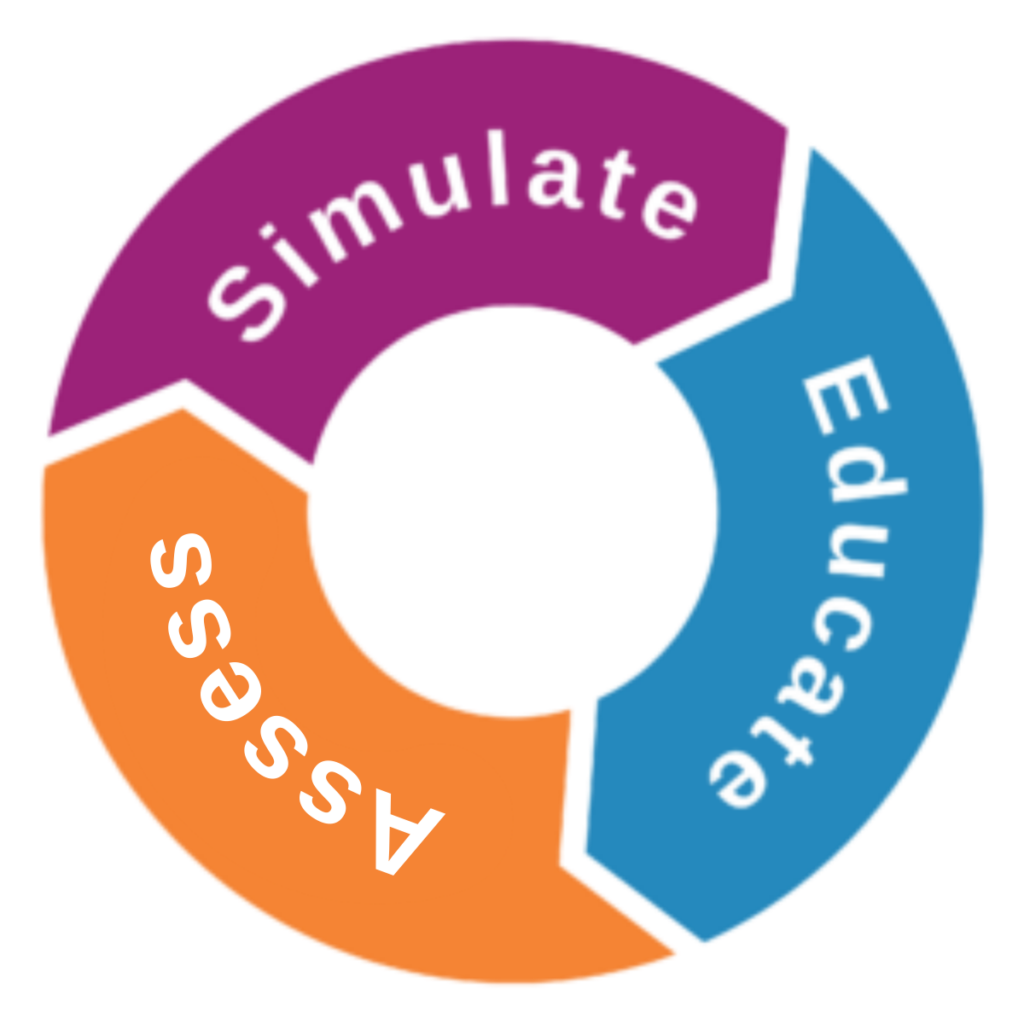
Reduce your risk with CybEssential's human-centric cyber security solutions
At CybEssential, we offer a range of affordable, human-centric solutions to educate your employees and help reduce your company’s risk of cyber attack. Discover which solution suits your organisation best.

ALREADY HAVE A LEARNING MANAGEMENT SYSTEM?
Get advanced security awareness training modules with seamless integration
CybEssential goes beyond the conventional one-size-fits-all licensing approach, offering you a range of company-branded training modules that seamlessly integrate into your existing LMS.
Our training is continually refined based on real-world scenarios experienced by the penetration testers and incident responders in our sister company, Sentaris.
Not sure where to start?
Ask about a tailored curriculum or security awareness program to meet your organisation’s unique requirements.
TEST AGAINST REAL PHISHING ATTACKS
Gauge awareness and reduce risk with real-world phishing simulations
Elevate your cyber security readiness with our real-world phishing and spear phishing simulations. These fully managed phishing simulations help empower your team to recognise and respond to threats effectively, reducing your risk of cyber attacks.


EMAIL AUTHENTICATION MADE EASY
Help protect your brand against email domain impersonation
Tired of wrestling with the complexities of DMARC and SPF?
Did you know that it is common for Business Email Compromise (BEC) attacks to try and impersonate your domain?
Whilst enabling SPF and DMARC can be scary, it’s a way for reducing the risk of BEC against you and your customers.
CybEssential is here to make it easy for you.
Why CybEssential
Experienced Professionals
Our team comprises of seasoned educators and cyber security professionals who understand the nuances of security awareness training and email security inside out.
Tailored Strategies
We don't believe in one-size-fits-all solutions. Our guidance is tailored to your business's unique needs, ensuring maximum effectiveness.
Practical Implementation
We provide actionable steps, clear guidelines, and hands-on support to seamlessly integrate our solutions into your cyber security strategy.
Backed by Experts
CybEssential is proudly supported by its industry-leading sister company, Sentaris, who is actively engaged in addressing real-world cyber security challenges and threats.
Download Your FREE Guide to Reducing Employee Cyber Security Risks
Learn how to boost your organisation’s security posture against human error and evolving cyber threats.

Start protecting and empowering your most important asset, your people.
Talk to us today about a free consultation, Human Risk Assessments, bespoke training program, phishing and more!