Fortify your email security with CybEssential's expert authentication service
In today’s digital world, unauthenticated emails can threaten your business’s reputation, exposing you to domain impersonation, phishing, and credibility risks.
CybEssential offers a robust Email Authentication service, fortifying your email defence and ensuring any messages sent to your valuable staff, customers and partners are authentic.

If your DMARC record has not been configured properly,
CybEssential's Email Authentication service is a must
Managing SPF and DMARC configurations can often be a complex task. However, with CybEssential, we simplify the process by providing expert guidance and support every step of the way. By choosing our services, your organisation can unlock a multitude of benefits.
Boost Recipient Trust
Build trust with your recipients, as they can be confident that the emails they receive are genuinely from your organisation.
Elevate Email Deliverability
Bypass spam filters, ensuring better deliverability rates as we facilitate the implementation of SPF, DKIM, and DMARC.
Combat Domain Spoofing
Prevent email domain spoofing by ensuring the legitimacy and dependability of emails sent on your behalf.
Amplify Brand Protection
Prevent cybercriminals from tarnishing your image through email domain spoofing and fraudulent emails.
Protect Against Phishing
Significantly reduce the risk of phishing attacks by using the reliable digital signature provided by DKIM to confirm the legitimacy of emails.
Enhance Email Monitoring
Track email activity and possible domain abuse with the help of DMARC policies to stay ahead of emerging threats.

Email authentication can be complicated, don't do it alone
Email Authentication can often be a daunting and complex task. However, you don’t have to tackle it alone. CybEssential is here to offer expert guidance and support. Our step-by-step guidance and proactive monitoring simplify the process, ensuring the security and credibility of your email communications.
Empowering email security through collaboration
Our collaborative approach helps your organisation leverage advanced DMARC, SPF, and DKIM configurations to put you in complete control of unauthenticated emails and their treatment by recipient servers.
By meticulously verifying the authenticity of emails, you can establish their origin, reinforcing recipient confidence, overall security, and seamless deliverability.
How we work
Our experts are dedicated to simplifying your email authentication experience. Our streamlined approach comprises of six easy steps that empower your business with flawless email delivery and domain protection. Let's embark on this journey together and unlock the true potential of your communication.
We work with you to assess your outbound email systems to identify both internal and external senders.
We help you to develop and implement crucial DNS configurations (SPF, DKIM, DMARC) to lay a solid foundation for smooth email delivery and improved security.
Over a 3 month period we record incoming DMARC report data, so we can pinpoint any compliance issues, delivery glitches, and potential threats.
By leveraging data-driven insights from the Monitoring phase, we facilitate your first DNS configuration enhancements to optimise your results.
Sit back as we record domains for another 3 months to ensure no new servers are identified.
Finally, we can decisively thwart email domain impersonation by meticulously analyzing the data amassed during the Review phase and refining your DNS configuration.
Expert guidance at every step
With CybEssential as your trusted partner, you gain access to a team of seasoned experts ready to navigate this complexity on your behalf.
From the initial implementation to continuous refinement, we help you develop of a robust and highly effective email authentication strategy, so you can rest easy, knowing your digital communications more robust.
FAQ
What is DMARC?
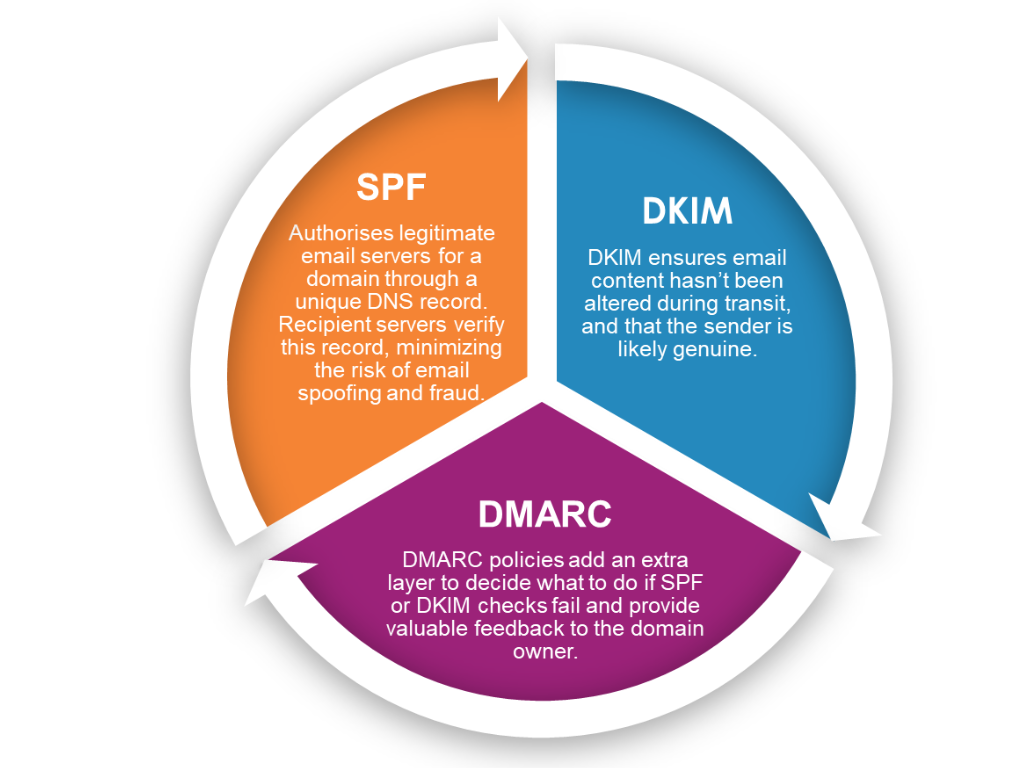
Domain-based Message Authentication Reporting & Conformance (DMARC) is an email security protocol. DMARC policies can instruct receivers to either deliver the email, quarantine it, or reject it entirely. Additionally, DMARC provides valuable reporting data, enabling domain owners to monitor email activity and potential abuse of their domain.
What is SPF?
Sender Policy Framework (SPF) is an email authentication protocol that prevents email spoofing. It authorises legitimate email servers for a domain by adding a special DNS record. Recipient servers check this record to verify the authenticity of incoming emails, reducing email fraud risk.
What are the possible Implications assocated with domain spoofing?
Domain spoofing is a sophisticated cyber threat that can directly impact your organisation’s credibility, security, and relationships. Cybercriminals employ this technique to forge emails or websites that appear to originate from your own domain, deceiving recipients into believing these communications are legitimate.
The implications of domain spoofing for your organisation are significant:
Reputation Damage: Spoofed emails can tarnish your brand’s reputation and erode the trust your stakeholders place in your communications. Recipients may associate your domain with fraudulent activities, causing long-term harm.
Data Breach Risk: Domain spoofing could trick your employees into sharing sensitive information, such as login credentials or financial data, with malicious actors. This puts your organisation at risk of data breaches and potential financial losses.
Malware Distribution: Cybercriminals often embed malware or phishing links within spoofed emails, infecting recipients’ systems or networks. Such security breaches could lead to operational disruptions and compromise confidential data.
Client and Partner Relationships: Spoofed emails sent from your domain might target your clients, partners, or vendors, damaging crucial relationships and affecting business collaborations.
Regulatory Compliance: Falling victim to domain spoofing may lead to regulatory non-compliance, especially if sensitive customer data is compromised.
As you consider email authentication solutions, addressing domain spoofing becomes paramount. Protecting your domain against such threats ensures that your communication channels remain secure, trustworthy, and reliable. By taking proactive measures, you fortify your domain’s integrity and contribute to a safer digital environment for both your organisation and your stakeholders.
What is DKIM?
DomainKeys Identified Mail (DKIM) is like a digital signature for an email. When an email is sent, the sender’s email server signs the message with a private key unique to the domain. The recipient’s email server can then verify the signature using the corresponding public key. If the verification passes, it means the email’s content hasn’t been altered during transit, and the sender is likely genuine.
What is email Authentication?
Email authentication is a set of techniques and protocols used to verify the authenticity of an email’s sender and the integrity of its content. These authentication methods help prevent email fraud, phishing, and other malicious activities by confirming that the email is genuinely from your organisation and hasn’t been tampered with during transmission.
Why is Email Authentication important?
If an organisation doesn’t have email authentication measures in place, it can lead to several significant issues, as follows:
Phishing attacks: Without email authentication, it becomes easier for attackers to impersonate legitimate sources and send phishing emails. Phishing attempts can trick employees into revealing sensitive information, login credentials, or even lead to malware installations.
Business email compromise (BEC): Email authentication helps prevent BEC attacks where cybercriminals impersonate key personnel in the organisation, such as executives or finance personnel, to trick employees into making fraudulent transactions.
Domain spoofing: Lack of authentication makes it simple for attackers to forge the sender’s domain, making it appear as though the email is from a trusted source. This can deceive recipients into trusting malicious emails.
Brand reputation damage: If your domain is frequently used for spam or phishing emails due to a lack of authentication, it can damage your brand’s reputation and trustworthiness.
Data breaches: Inadequate email authentication can make it easier for attackers to gain unauthorised access to sensitive company data and confidential information.
Loss of customer trust: If customers receive emails from attackers posing as your organisation, it can lead to a loss of trust in your brand and result in customers being wary of interacting with your emails in the future.
Regulatory non-compliance: Many industry regulations, such as GDPR (General Data Protection Regulation), require organisations to implement security measures, including email authentication, to protect customer data. Non-compliance can lead to legal consequences and financial penalties.
Internal communication risks: Without proper authentication, employees may receive fake internal emails that appear to be from their colleagues, leading to confusion and potential security breaches.
Reduced email deliverability: If your domain is frequently abused for spam or phishing, email providers may block or flag your emails as suspicious, leading to reduced deliverability rates for legitimate communications.
Increased support workload: Employees and customers may contact your support team to verify the legitimacy of suspicious emails they receive, increasing the support workload and wasting valuable resources.
To mitigate these issues, organisations should implement proper email authentication protocols such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) to enhance email security and protect their brand’s reputation.
Need secure and efficient email delivery?
At CybEssential we provide Email Authentication solutions to businesses of all sizes.